September 2023
Innovation Matters: Ransomware "Kill Switch"
15/09/23 13:13

“Wicked” Business Problem:
Organizations running flat networks are especially vulnerable to high-impact attacks that rely on lateral movement like ransomware.
Innovative Approach:
The ability to move from a flat network to a layer-3 isolated (micro-segmentation) network (IT/OT) in a matter of hours with NO downtime or 3rd party agent software.
Vetted Solution:
Airgap’s elegant approach is truly innovative and worthy of consideration. Using DHCP to build a layer-3 overlay network, they can transform a legacy network into a virtual Purdue compliant environment. Prebuilt logic provides the ability to prevent ransomware propagation and introduces a “kill switch”, which can be activated in the case of a ransomware outbreak.
Call To Action:
Educate yourself on Airgap's innovative approach to layer-3 isolation and segmentation.
Facilitated Innovation & Structured Choice
15/09/23 12:44
What is it?
· A field-proven methodology that identifies self-funding business cases and drives transformational change. I have used this method successfully in my practice for many years now.
How does it work?
· Facilitates a dialog with key stakeholders who can affect organizational change.
· Aligns the organization’s mission with stakeholder capabilities (known & latent).
· Determines what MUST be true in order for the organization to achieve its mission objectives.
· Optimizes value across diverse stakeholder communities.
· Leverages rapid prototyping to Fail/Succeed Fast as measured against key proof points.
· Delivers in 30-90 Day Proof of Value (PoV) sprints.
· Produces a pipeline of Innovation Candidates to support a transformation plan of record.
· Populates an organization specific Curated Service Catalog that is fit for purpose and provides choice
· Institutionalizes a bespoke service selection methodology that ensures the Optimal Choice is made to capture Maximum Value as defined by the relevant stakeholders.
Here is an example of a Curated Service Catalog for the manufacturing sector:

So what?
By distilling the world of possibilities down to business-friendly options, organizations can realize more value faster and at scale. I plan on sharing some of the most interesting, timely and relevant candidates via a new blog series called Innovation Matters.
· A field-proven methodology that identifies self-funding business cases and drives transformational change. I have used this method successfully in my practice for many years now.
How does it work?
· Facilitates a dialog with key stakeholders who can affect organizational change.
· Aligns the organization’s mission with stakeholder capabilities (known & latent).
· Determines what MUST be true in order for the organization to achieve its mission objectives.
· Optimizes value across diverse stakeholder communities.
· Leverages rapid prototyping to Fail/Succeed Fast as measured against key proof points.
· Delivers in 30-90 Day Proof of Value (PoV) sprints.
· Produces a pipeline of Innovation Candidates to support a transformation plan of record.
· Populates an organization specific Curated Service Catalog that is fit for purpose and provides choice
· Institutionalizes a bespoke service selection methodology that ensures the Optimal Choice is made to capture Maximum Value as defined by the relevant stakeholders.
Here is an example of a Curated Service Catalog for the manufacturing sector:

So what?
By distilling the world of possibilities down to business-friendly options, organizations can realize more value faster and at scale. I plan on sharing some of the most interesting, timely and relevant candidates via a new blog series called Innovation Matters.
Point of Origin Hacking (POOH)
05/09/23 07:59
Historically, infosec risk managers have stressed only focusing on the most likely and impactful threats. However, this practice often misses “obvious” vulnerabilities that lead to catastrophic failure. When realized, these threats are often branded as “black swan” events, which some believe could never be predicted. This lack of imagination is no longer acceptable, given advances in modeling and simulation capabilities.
Rather, novel, forward thinking and expanded threat catalogs need to be developed and adopted. This is the fundamental tenant behind POOH (Point of Origin Hacking). The concept goes like this; If you have a properly motivated adversary, they will (eventually) develop or obtain a (theoretical) capability that they will use against you. So, build systems that take into account theoretical vulnerabilities, as they will likely become practical in the fullness of time.
Rather, novel, forward thinking and expanded threat catalogs need to be developed and adopted. This is the fundamental tenant behind POOH (Point of Origin Hacking). The concept goes like this; If you have a properly motivated adversary, they will (eventually) develop or obtain a (theoretical) capability that they will use against you. So, build systems that take into account theoretical vulnerabilities, as they will likely become practical in the fullness of time.
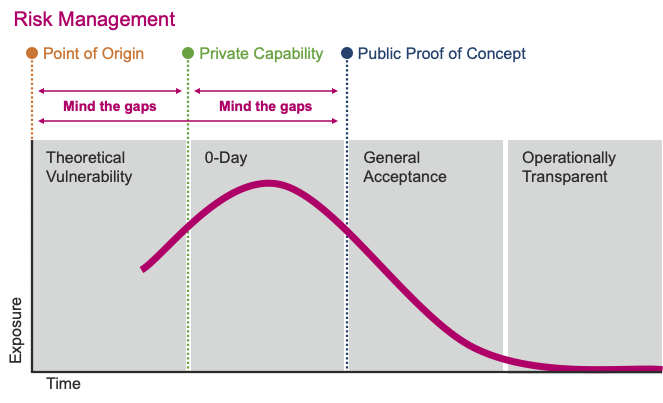
Example: In a post quantum world, many encryption algorithms will be worthless as a protection mechanism. Knowing this, organizations should choose algorithms that are post quantum secure.
So the next time someone tells you that an alien invasion, zombie apocalypse and giant meteors are out of scope for your threat catalog, just remind them that those items look a lot like volcanoes, pandemics, unprovoked war, trucker strikes, train derailments, global warming...Plan accordingly, because you never see the one that gets you.