Point of Origin Hacking (POOH)
05/09/23 07:59
Historically, infosec risk managers have stressed only focusing on the most likely and impactful threats. However, this practice often misses “obvious” vulnerabilities that lead to catastrophic failure. When realized, these threats are often branded as “black swan” events, which some believe could never be predicted. This lack of imagination is no longer acceptable, given advances in modeling and simulation capabilities.
Rather, novel, forward thinking and expanded threat catalogs need to be developed and adopted. This is the fundamental tenant behind POOH (Point of Origin Hacking). The concept goes like this; If you have a properly motivated adversary, they will (eventually) develop or obtain a (theoretical) capability that they will use against you. So, build systems that take into account theoretical vulnerabilities, as they will likely become practical in the fullness of time.
Rather, novel, forward thinking and expanded threat catalogs need to be developed and adopted. This is the fundamental tenant behind POOH (Point of Origin Hacking). The concept goes like this; If you have a properly motivated adversary, they will (eventually) develop or obtain a (theoretical) capability that they will use against you. So, build systems that take into account theoretical vulnerabilities, as they will likely become practical in the fullness of time.
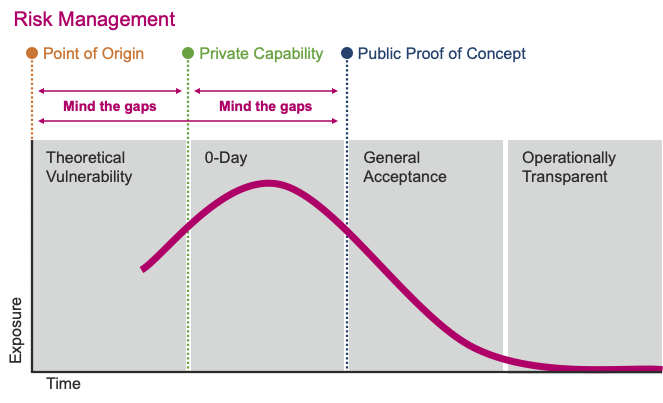
Example: In a post quantum world, many encryption algorithms will be worthless as a protection mechanism. Knowing this, organizations should choose algorithms that are post quantum secure.
So the next time someone tells you that an alien invasion, zombie apocalypse and giant meteors are out of scope for your threat catalog, just remind them that those items look a lot like volcanoes, pandemics, unprovoked war, trucker strikes, train derailments, global warming...Plan accordingly, because you never see the one that gets you.